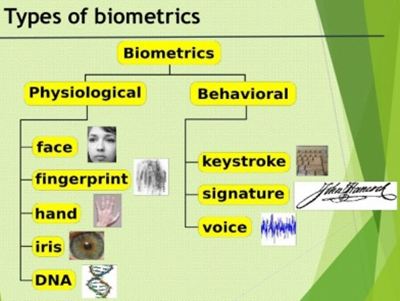
Security Surveillance (Biometrics )
Person-recognition Systems
=========================
Person-recognition systems are a major spin-off from improvements in computing power,
together with research into biometrics (the measurement of biological characteristics) and
the development of software to exploit this research, during the 1980s and 1990s. These
systems works by measuring features that are unique to an individual and then using the
data for security purposes.
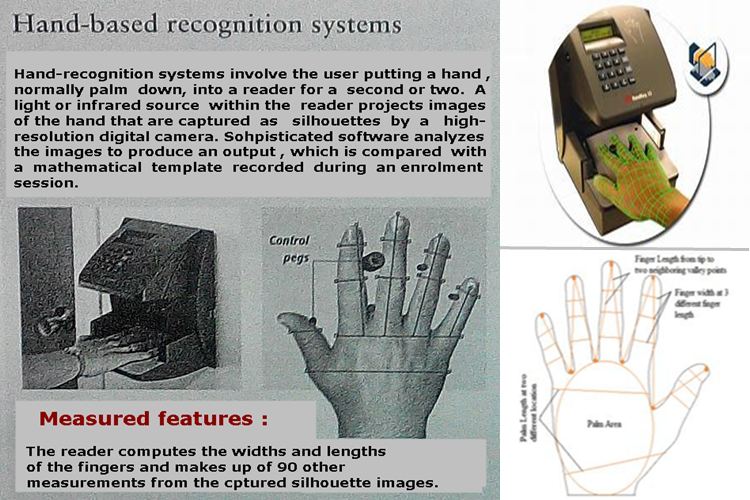
Hand-based Recognition Systems
============================
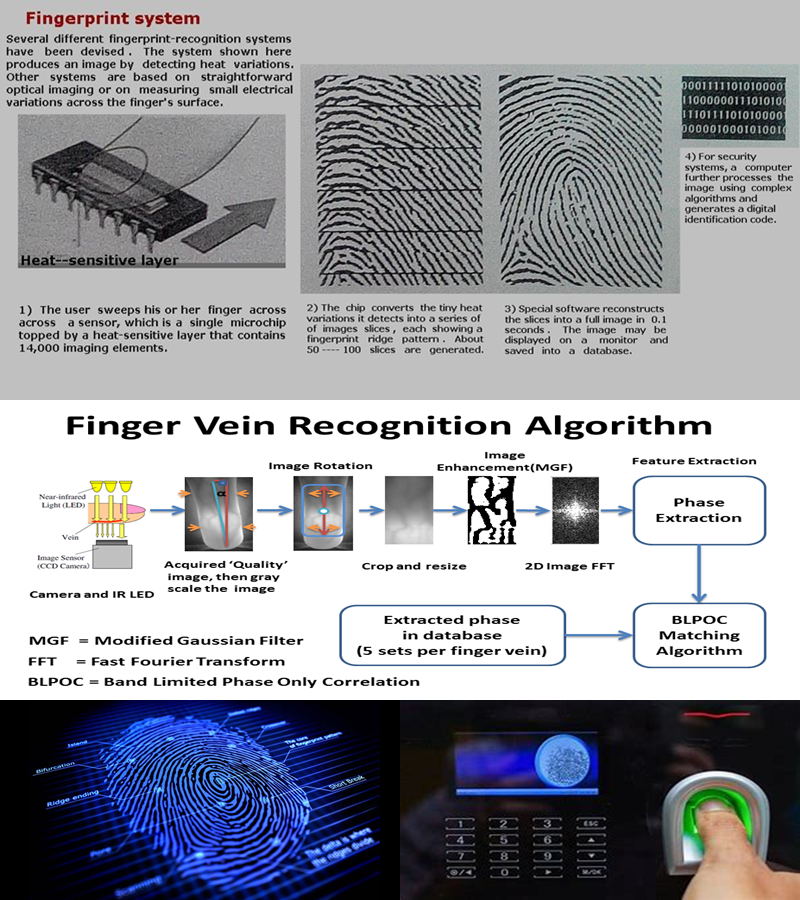
Fingerprint System
====================
In broad terms, all person-recognition systems work in the same way. A user must first be enrolled
onto the system by either speaking into a microphone or by having a feature, such as an eye or a
hand, scanned, analyzed, and turned into a digital code. The code is stored on a database,
sometimes with a supplementary identifier, such as a personal identification number (PIN). When
the user wishes to gain access to a protected environment, such as a building or a computer
network, the scan is repeated and a second code generated. This code may then be compared
either with a particular stored code (by reference to the additional identifier supplied by the user)
or with all the codes on the database, which takes a little longer but requires no other identifier.
Modern systems have very low false-accept and false-reject rates, which are the main indicators
of their effectiveness.
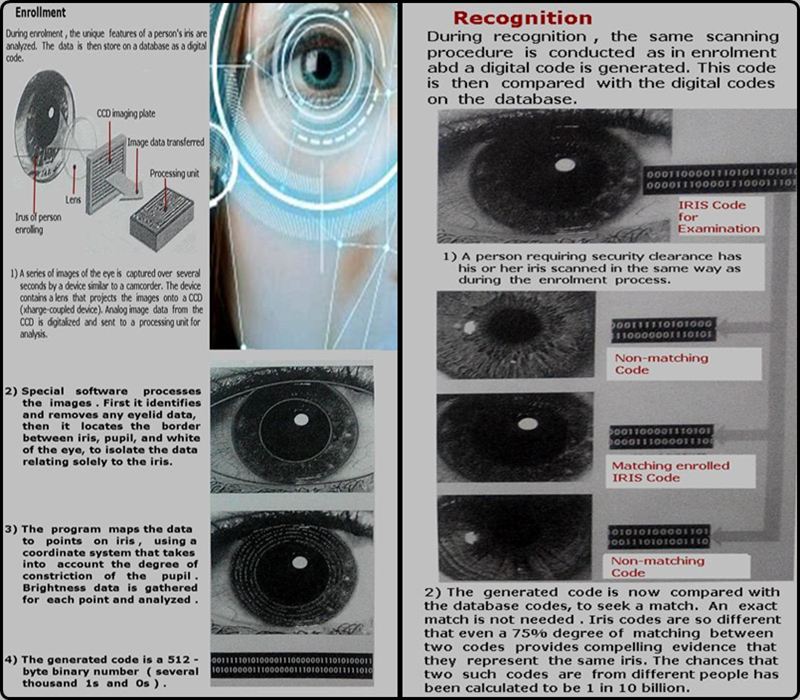
Iris-based Recognition Systems
==================================
The iris is the colored ring of tissue surrounding the pupil of the eye. Every iris has a unique pattern
of features such as striations, freckles, and so on, that remains constant throughout life and cannot
be faked or mimicked. This iris is thus a highly effective personal identifier.